Introduction
You've been there. The Head of Sales Operations, marketing or operations requests a new mapping software solution. Immediately, your mind races through the IT governance checklist:
- Is it secure?
- How will it integrate with our Salesforce instance?
- What are the data residency and compliance implications? Is this going to be another unsupported, resource-draining application my team gets stuck with?
You're tasked with being a strategic partner to the business, but you spend your days reacting to requests and mitigating the risks of "shadow IT."
What if you could proactively provide a single, secure, and scalable mapping software platform that integrates seamlessly with your Salesforce instance, or can be used independently of it? This guide will cover the essentials you need to understand when choosing the right mapping software.
-
1. New reality
Why You Need to Look Beyond Traditional Bi Tools
View chapter about "1. New reality" -
2. Raw data
How to get from
View chapter about "2. Raw data"
data to decision -
3. Questions to ask
Answering your
View chapter about "3. Questions to ask"
toughest questions -
4. Business case
From cost center
View chapter about "4. Business case"
to profit driver
Chapter 1
The New Reality for I.T. Why You Need to Look Beyond Traditional Bi Tools

1. What is Mapping Software for I.T. Leaders?
For an IT leader, mapping software is not just a data visualization tool. It's a secure, cloud-based platform for location intelligence that provides robust administrative controls, enterprise-grade security, and seamless integration with Salesforce. Think of it as a specialized BI tool for geospatial analysis that is built from the ground up to meet the stringent security and governance requirements of a modern IT department.

2. The High Cost of Good Enough Solutions
When business teams need to analyze location data, they turn to what's available. These "good enough" solutions are a significant source of risk and operational drag for IT:
- Pervasive security risks: The use of unsanctioned, consumer-grade mapping tools ("shadow IT") means employees may be uploading sensitive customer lists, sales figures, and strategic plans to platforms without proper security vetting. This creates a massive, unmanaged attack surface, increasing the risk of a data breach.
- Crushing support burden: Legacy desktop mapping software is notoriously difficult to deploy, patch, and maintain across a distributed workforce. It creates a constant stream of support tickets for everything from installation issues to data import errors, draining valuable IT resources.
- Data silos and integration chaos: When each team uses its own tools, data becomes fragmented and disconnected from your systems of record. This leads to inconsistent reporting and makes it impossible to establish a single source of truth, undermining the very purpose of data analysis.

3. The Strategic Advantage of a Secure, Centralized Mapping Platform
By implementing a centralized platform like eSpatial, you can directly address these challenges:
- Centralize and secure data: Bring all mapping activity into a controlled environment with robust security features like SSO, granular user permissions, and end-to-end data encryption. This eliminates shadow IT and gives you complete visibility and control.
- Guarantee data governance: With certified integrations for systems like Salesforce, you can ensure that business users are always working with accurate, up-to-date data from your single source of truth, eliminating data drift and inconsistency.
- Empower users, liberate IT: An intuitive, self-service platform allows business users to create their own maps and dashboards. This satisfies their needs while dramatically reducing their reliance on IT for ad-hoc reports, freeing up your team to focus on high-value strategic initiatives.
How It Works
Step 1
Sign up & Upload
Your Data
Create a free account on our website, no credit card required. Then, upload your data from spreadsheets, CRMs, or other sources. eSpatial supports multiple file types, so you can get started quickly with minimal prep.
Step 2
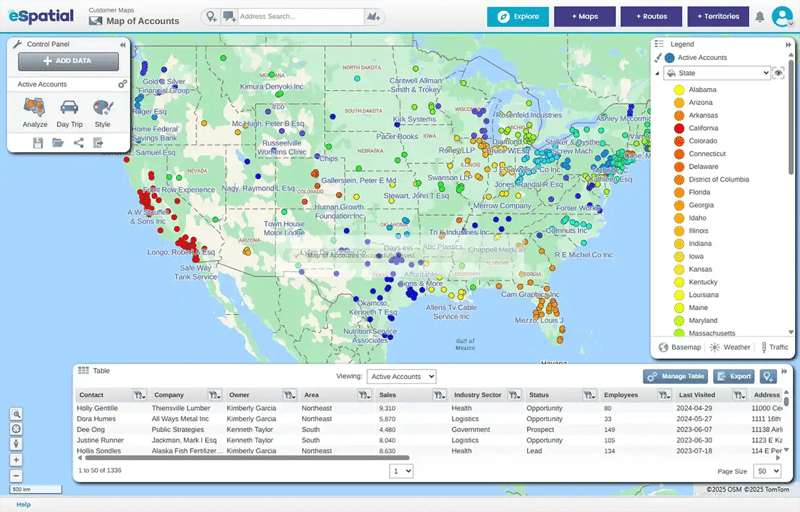
Map And
Customize
Plot your data points like stores, clients, or assets on an interactive map. Use built-in filters, labels, and styling tools to highlight trends, customize views, and layer in details like sales territories or customer segments.
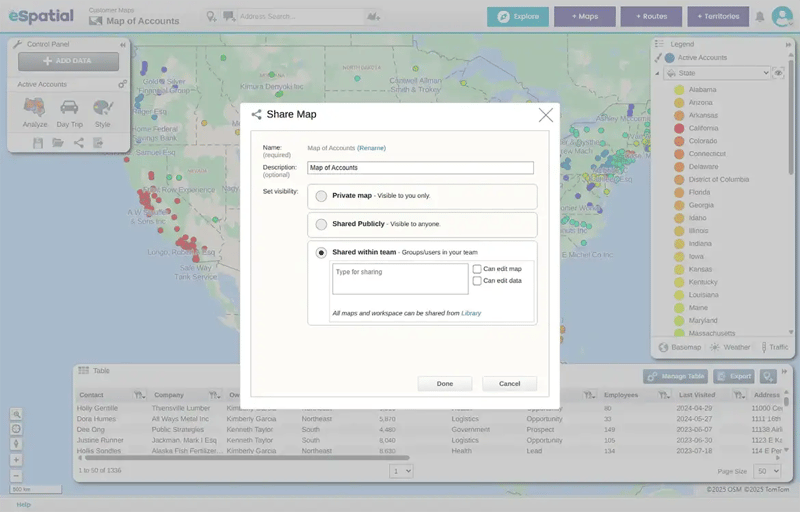
Step 3
Analyze And
Share Insights
Leverage powerful analytics to create heat maps, territory plans, or optimized routes. Easily share your visual insights through exportable formats or interactive maps to accelerate decision-making across your team.
Chapter 2
From Data Chaos to Clarity How Mapping Software Transforms the I.T. Role
A secure mapping platform allows you to confidently enable the business while maintaining strict control over the IT environment.
-
Enable a secure mobile workforce
Instead of sales reps emailing static, insecure spreadsheets of customer data, you can provide them with secure, interactive territory maps accessible via any device. Role-based permissions ensure they only see the data relevant to them, and access can be revoked instantly.
-
Integrate Salesforce data without compromising integrity
A robust integration allows for a real-time, bidirectional sync with your CRM. This ensures data integrity is maintained and that your maps always reflect the single source of truth, without requiring manual data dumps.
-
Visualize and manage IT assets
For IT teams managing physical assets, mapping software can provide a real-time, interactive dashboard of network infrastructure, data centers, or field equipment. This enables faster outage identification, optimised maintenance schedules, and more effective resource allocation.
Chapter 3
The I.T. Manager's Toolkit Key Features to Scrutinize

1. Security & Compliance
- Single sign-on (SSO): Look for SAML 2.0 support to integrate with your identity provider (e.g., Okta, Azure AD). This centralizes access control and simplifies user provisioning and de-provisioning.
- Granular user permissions: You need the ability to define roles and permissions at a granular level—controlling who can view, create, edit, and share specific datasets and maps.
- Data encryption: Confirm that data is encrypted both at rest (AES-256) and in transit (TLS 1.2+).
- Compliance certifications: Ask for third-party security certifications, such as SOC 2 Type II or ISO 27001, to verify the vendor's security posture.

2. Integration & API
- Certified connectors: Prioritize platforms with pre-built, certified connectors for your core business systems (especially Salesforce) to ensure reliability and support.
- Robust and documented API: A well-documented REST API is essential for building custom integrations and automating data workflows, reducing manual work for your team.

3. Implementation & Support
- Onboarding and training: Does the vendor provide comprehensive onboarding and training for users? A solution that users can adopt with minimal IT intervention is a huge win.
- Dedicated support: What are the support SLAs? Access to a dedicated Customer Success Manager can offload the support burden from your internal helpdesk.
Chapter 4
Building the Business Case From Cost Center to Strategic Partner
An investment in a secure mapping platform delivers a clear and compelling ROI for the IT department.
-
Drastically reduce IT
support ticketsQuantify the hours saved by eliminating requests for manual data pulls, report creation, and support for legacy desktop software.
-
Mitigate the cost of
a data breachThe average cost of a data breach is millions of dollars. A secure, centralized platform is a critical investment in risk mitigation and an essential component of a modern security strategy.
-
Increase operational
efficiencyBy automating data flows and empowering business users, you reclaim valuable time for your IT team, allowing them to focus on strategic projects that drive innovation and growth.
The I.T. Leader's Checklist
How to choose the right vendor
Question 1
Can you provide your full security documentation, including your SOC 2 report and the results of your latest penetration tests?
Question 2
Where is your data hosted, and what are your data residency options?
Question 3
Walk me through the technical details of your Salesforce integration. Is it a real-time, bidirectional sync?
Question 4
What is your standard support SLA for critical issues?
Question 5
What is on your product roadmap for the next 12 months, specifically regarding security and integration features?
Conclusion
For too long, I.T. has been forced to choose between enabling the business and protecting the organization. This is a false choice. By moving beyond a patchwork of insecure, unsupported tools and embracing a secure, centralized mapping platform, you can transform your role from a reactive firefighter to a strategic business partner. This is the most pragmatic and effective way to empower your business users with the insights they need, all while strengthening your company's security posture and freeing up valuable IT resources.

